
RightSignature- Mandatory enforcement of Two-factor authentication

The Definitive Guide to 2 Factor Authentication - by Arsen

Guide - Two-Factor Authentication: Methods and Myths

Two Factor Authentication Explained: Cracking the Code

The Ultimate Guide to Setting Up Two-Factor Authentication (2FA) for Apple ID
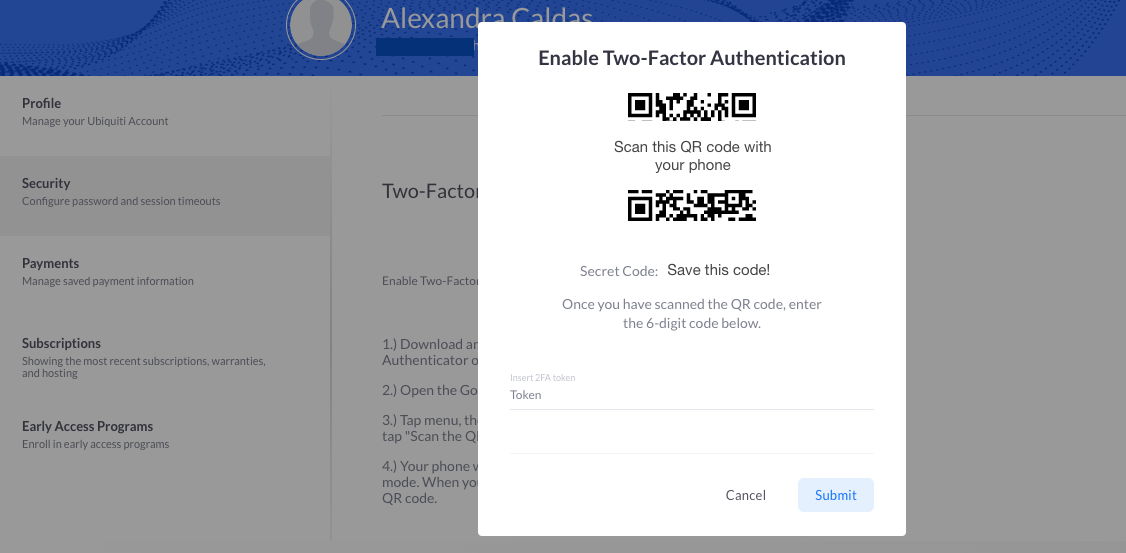
Token2, MFA tokens OATH-TOTP SHA-1 SHA-256, Hardware token for Ubiquiti Account 2FA, TOKEN2 MFA Products and Services
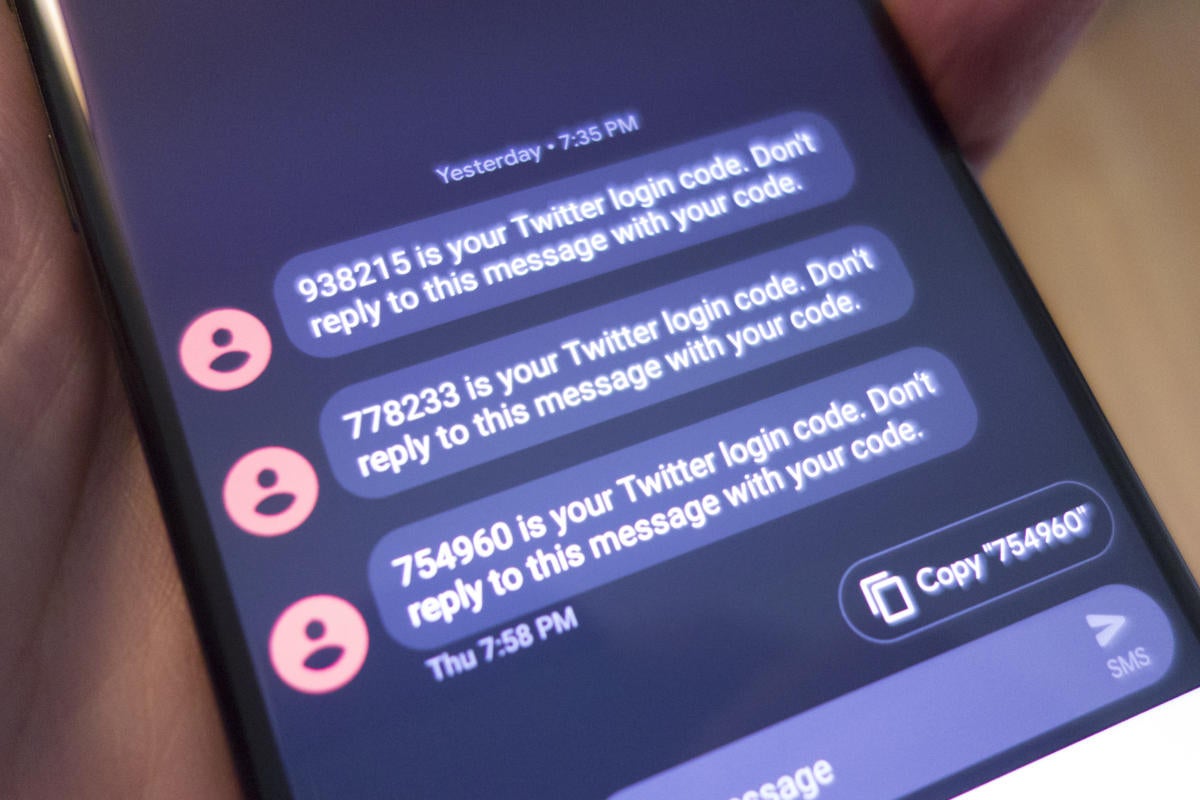
Two-factor authentication explained: How to choose the right level of security for every account

What is two-factor authentication (2FA)?

No, You Shouldn't Turn Off Two-Factor Authentication
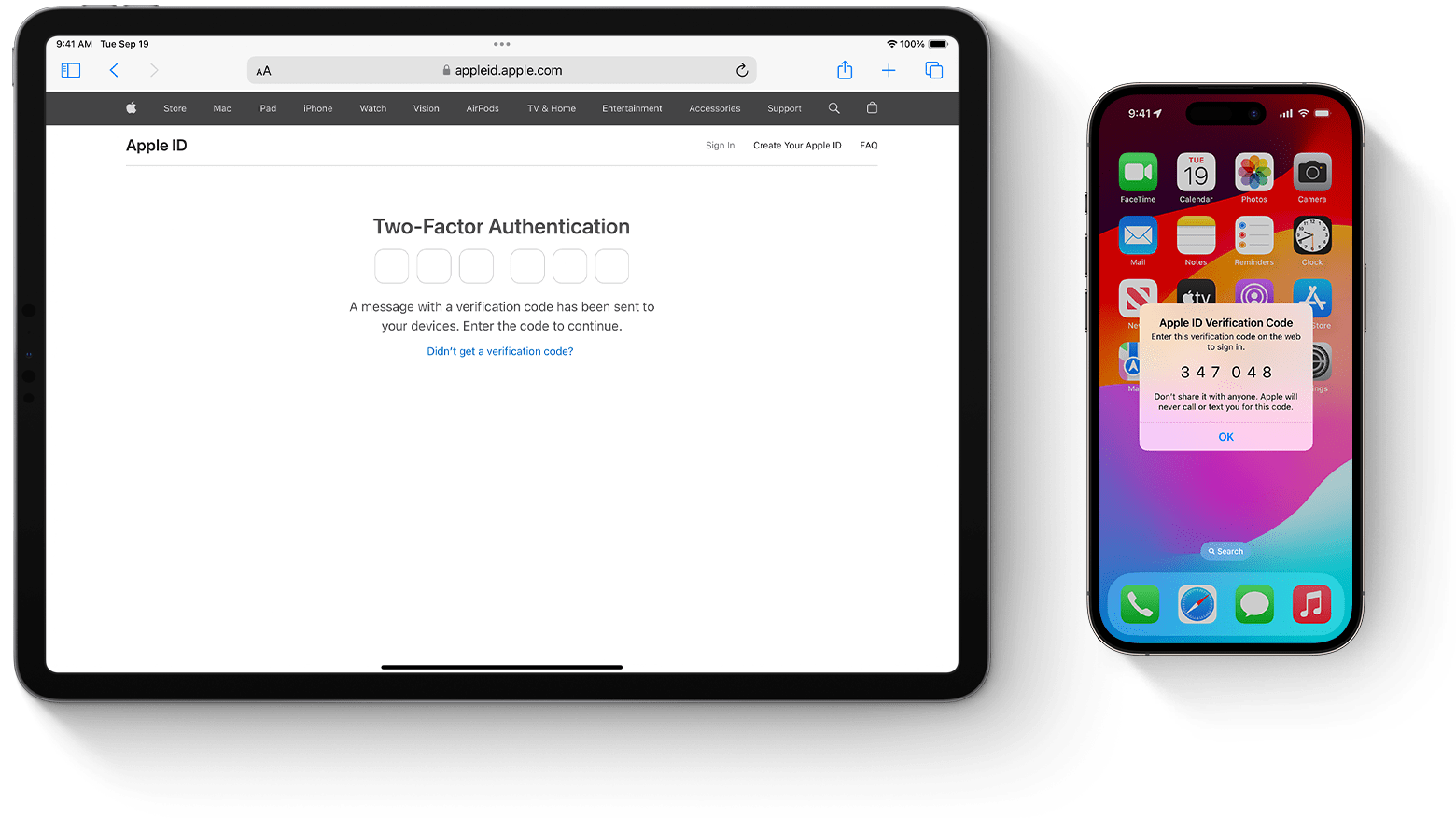
Two-factor authentication for Apple ID - Apple Support

Certified Authenticator Levels - FIDO Alliance

A Guide to Common Types of Two-Factor Authentication on the Web
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey

FIDO2: Authenticate easily with phishing-resistant security - Help Net Security
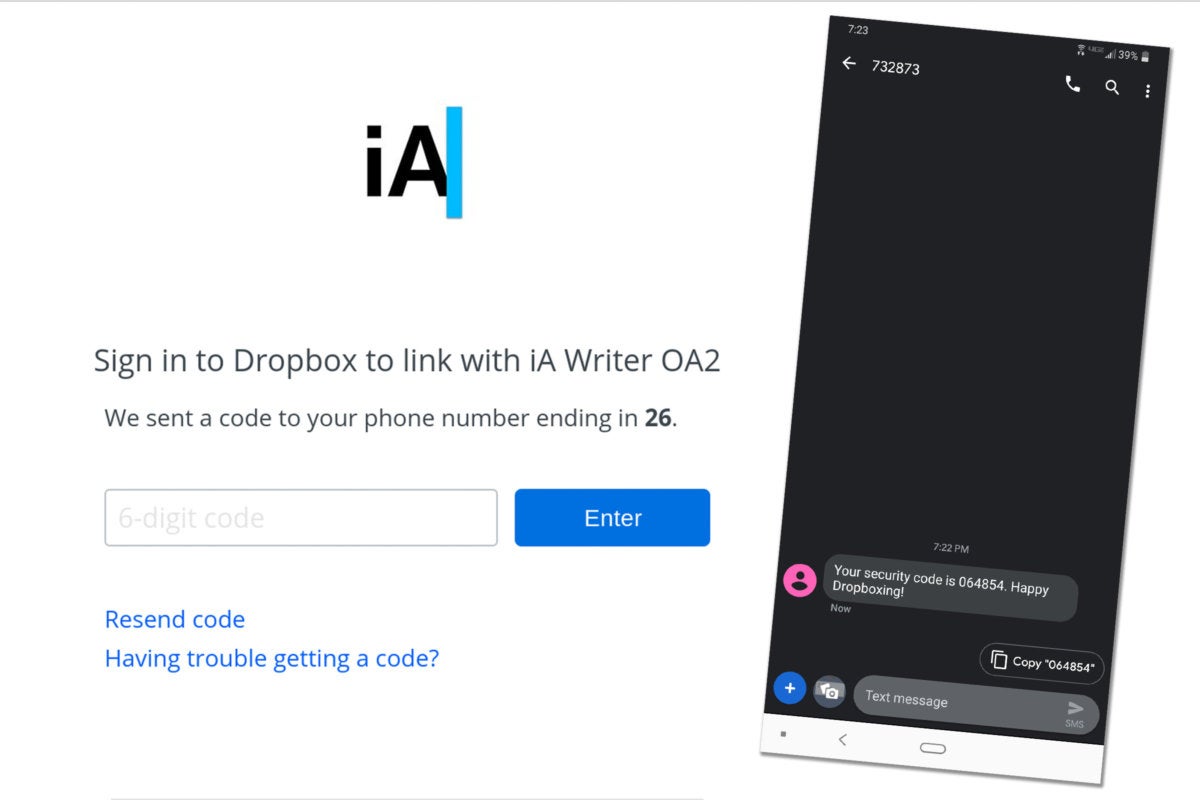
Two-factor authentication explained: How to choose the right level of security for every account
