
Authentification Guide — Two authenticators

Web Authentication: An API for accessing Public Key Credentials - Level 2
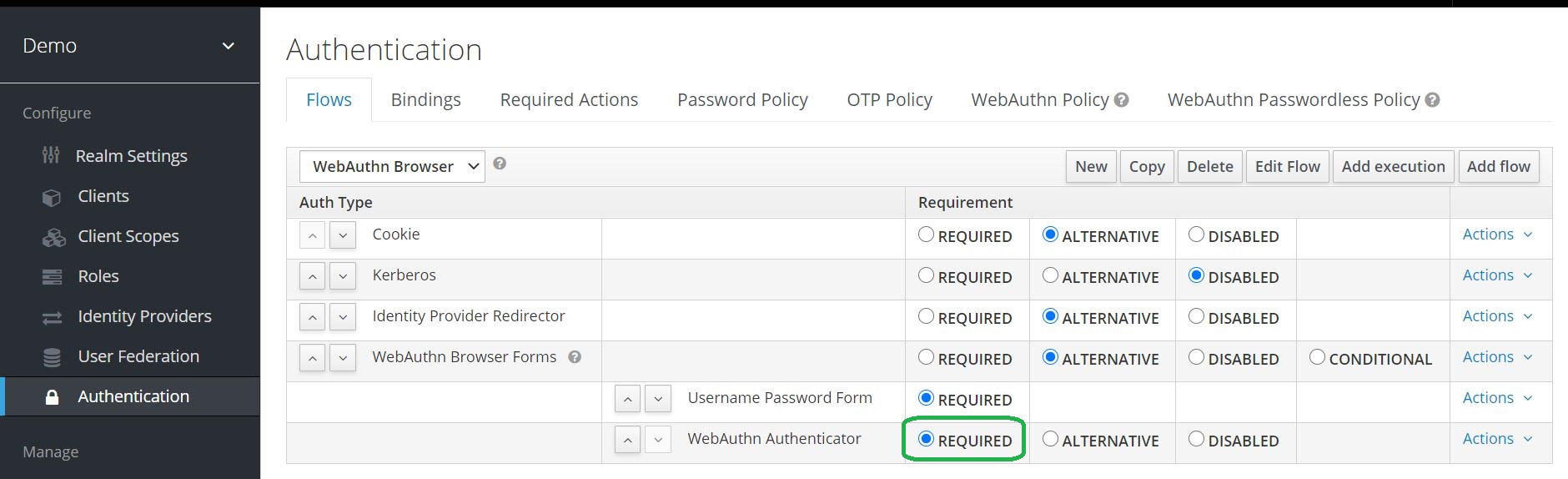
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog

FIDO2: Authenticate easily with phishing-resistant security - Help Net Security
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
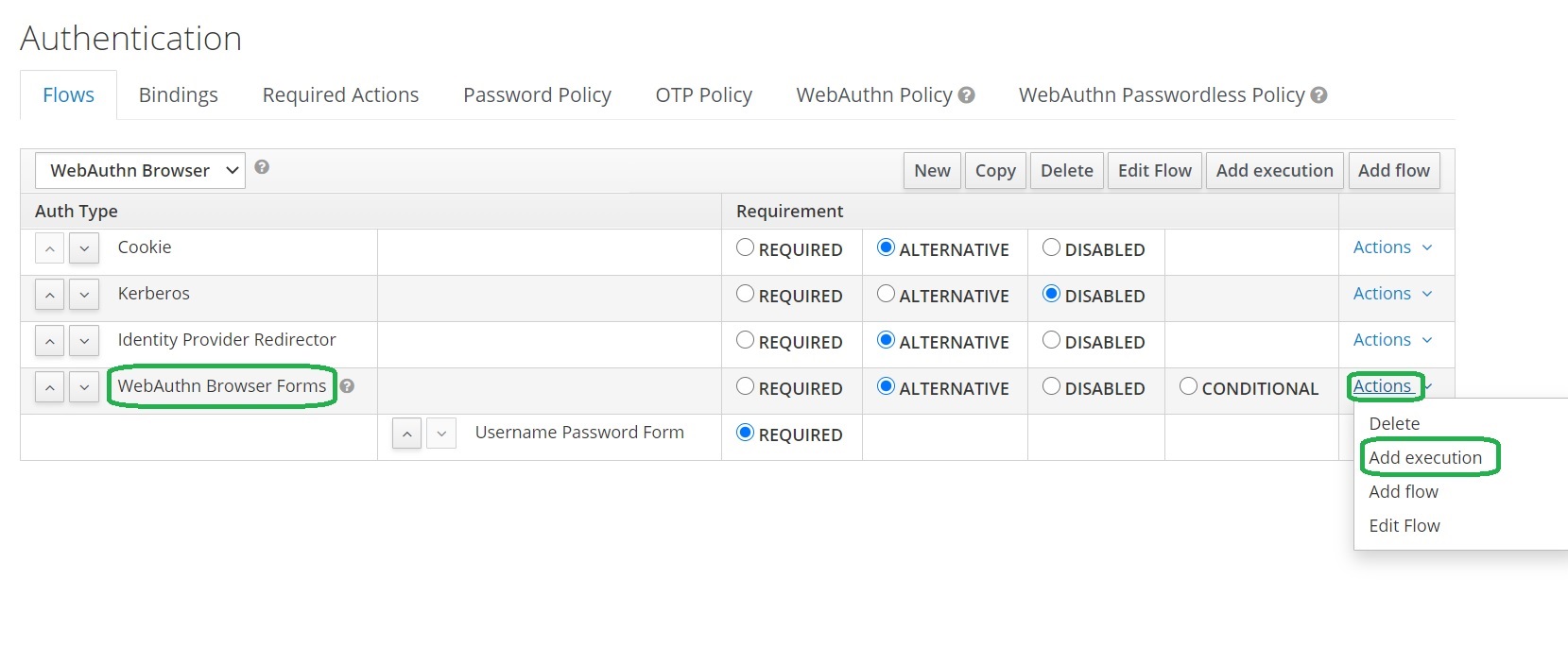
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog

Facebook two-factor auth

The Definitive Guide to 2 Factor Authentication - by Arsen

Client to Authenticator Protocol (CTAP)
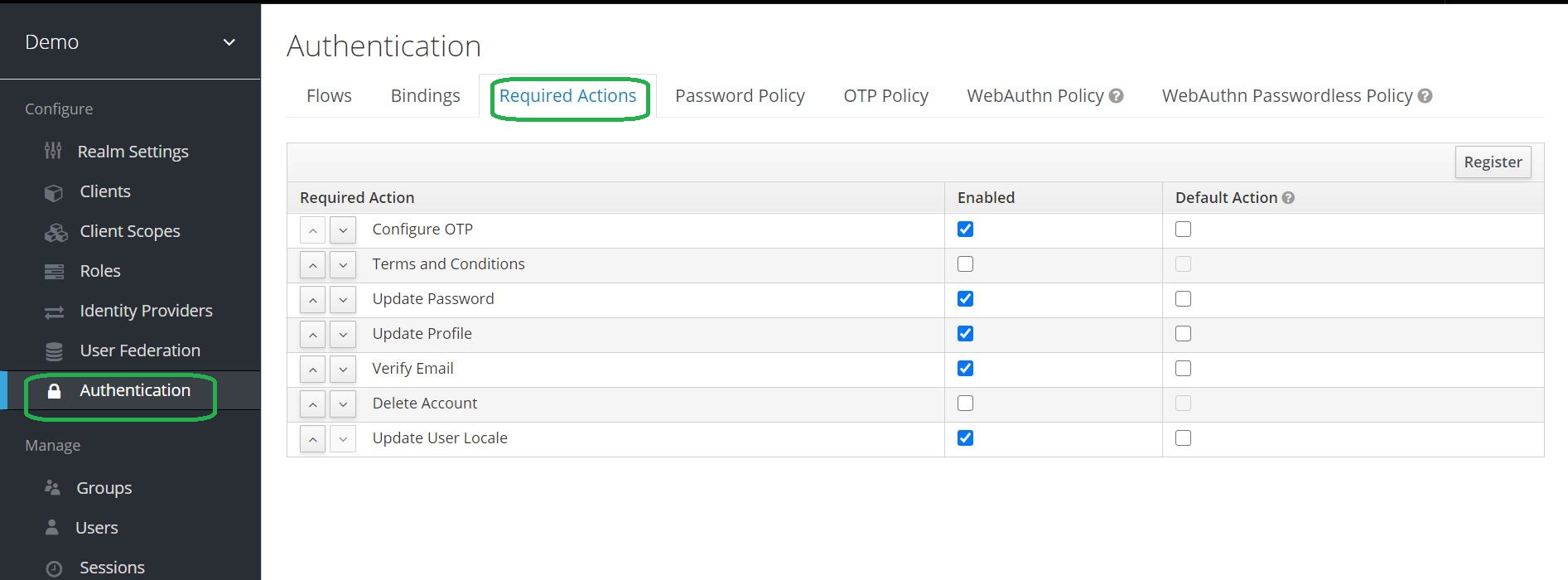
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog

Web Authentication: An API for accessing Public Key Credentials - Level 2

RightSignature- Mandatory enforcement of Two-factor authentication
