Heyserial - Programmatically Create Hunting Rules For Deseri
What's Next After Log4Shell? - vulnerability database
New Apache Struts RCE Flaw Lets Hackers Take Over Web Servers

CVE-2017-0146 - vulnerability database

Mark Twain Cave Signature: Searching for Sam Clemens's Long-Lost
Joshua Smith in Cursive - 97+ Name Signature Ideas ⚡
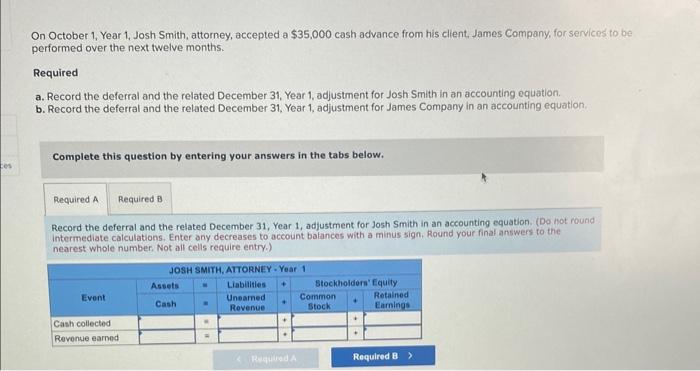
Solved On October 1, Year 1, Josh Smith, attorney, accepted
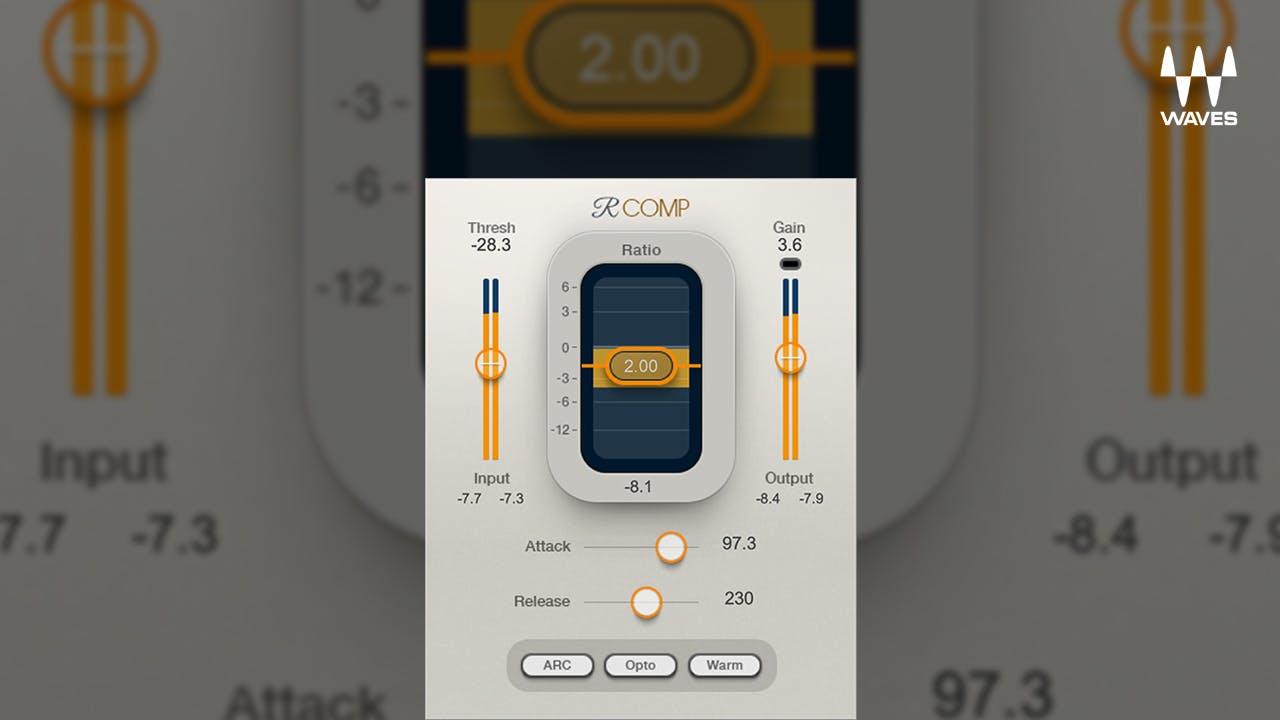
Renaissance Compressor Plugin - Waves Audio

Controller & Executive Controller

Josh Smith - QB Hit List

Citrix Application Delivery Controller and Citrix Gateway - Remote

How To Prioritize Vulnerabilities in a Modern IT Environment
litmus-experiments/java/geoNLP/sample_train.txt at master

Controller & Executive Controller
