
Things I Learned
PHP-Rake-IDF/idf.json at master · scrivna/PHP-Rake-IDF · GitHub

DIY Stacked Bracelets for Beginners - Happy Hour Projects

The Ultimate Guide to Creating the Perfect Bracelet Stack

The Ultimate Guide to Creating the Perfect Bracelet Stack

The Ultimate Guide to Creating the Perfect Bracelet Stack

The Ultimate Guide to Creating the Perfect Bracelet Stack

How to Stack Bracelets like a Pro

How to Stack Bracelets like a Pro

chatbot/dictionaries.py at master · fauchatbot/chatbot · GitHub
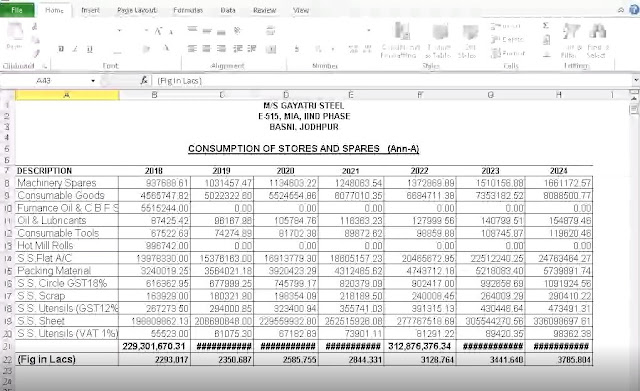
RATs and stealers rush through “Heaven's Gate” with new load - vulnerability database
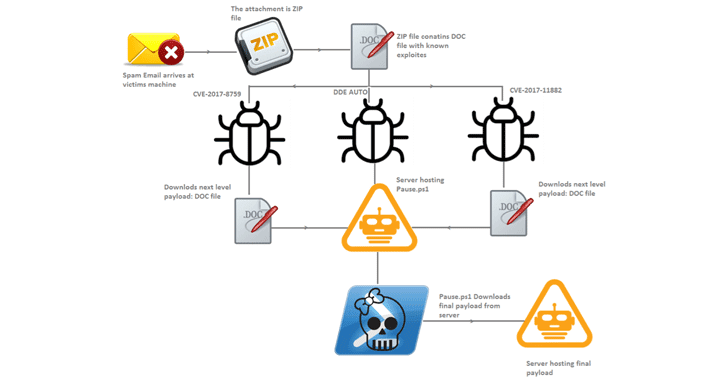
Hackers Exploiting Three Microsoft Office Flaws to Spread Zy - vulnerability database

Microsoft Exchange Server ProxyLogon vulnerability - exploit database

Informational: Impact of Spring Vulnerabilities CVE-2022-229 - vulnerability database
