
Authenticate This LV: READ the rules & use the format in post #1, Page 858
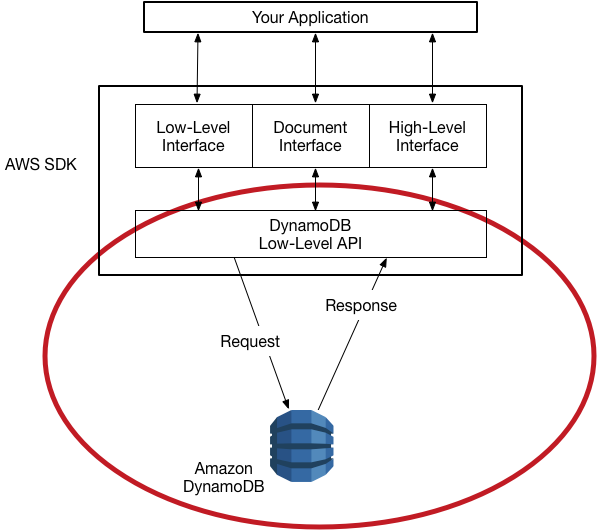
DynamoDB low-level API - DynamoDB
Kim TallBear Comments on Indigenous Citizenship in the Academy, 1 Year Later
Armv8.1-M architecture: PACBTI extensions - Architectures and Processors blog - Arm Community blogs - Arm Community
Authenticate This LV: READ the rules & use the format in post #1, Page 276
Using MySQLi to Insert Data: MySQL Database Management
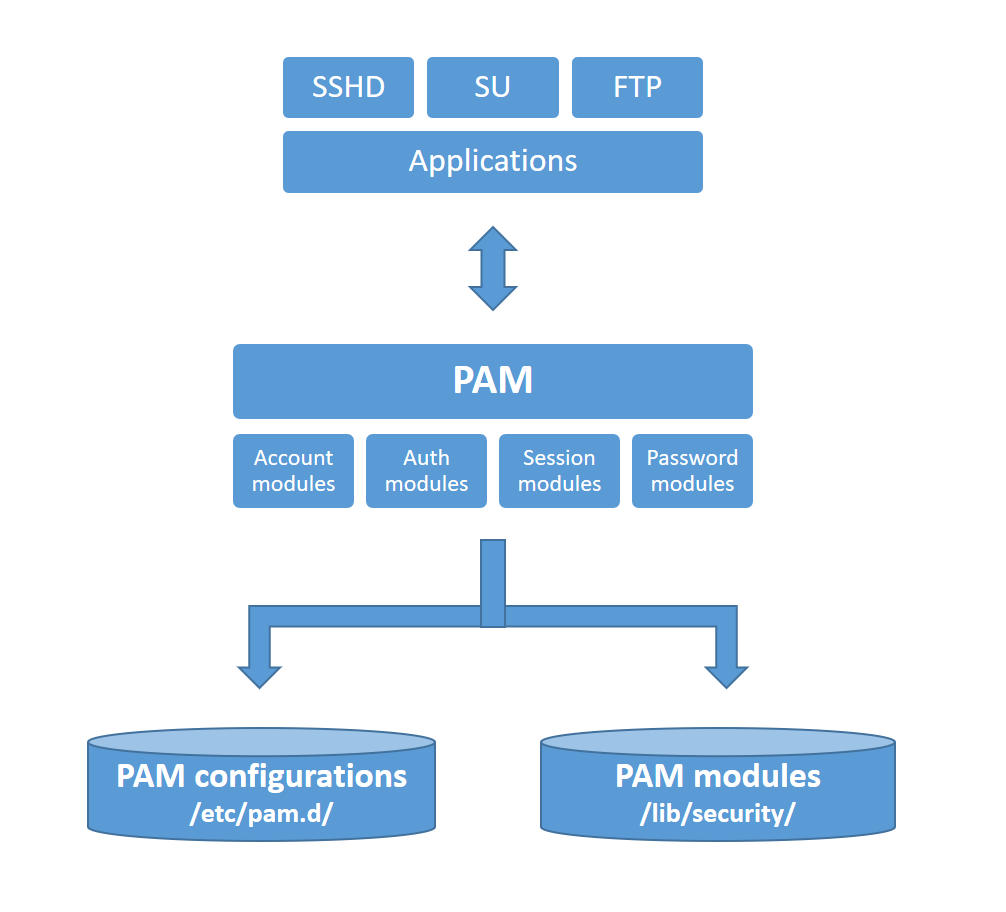
Linux PAM — How to create an authentication module, by Avi Rzayev

Authentication with Auth0 — Part #7 of 11, by Lohita

Authenticate This LV: read the rules & use the format in post 1, Page 112

Authenticate This LV: READ the rules & use the format in post #1, Page 427

What is DRM? Digital Rights Management Simplified - OTTVerse
Endpoint Security Explained

Why APIs are Your Biggest Security Risk
