
Authorities Fully Behead Hydra Dark Marketplace - vulnerability database

Threat Analysis: Equation Equals Backdoor - vulnerability database

Assess Your Risk From Ransomware Attacks, Powered by Qualys - vulnerability database

Ransomware-as-a-service: Understanding the cybercrime gig ec - vulnerability database
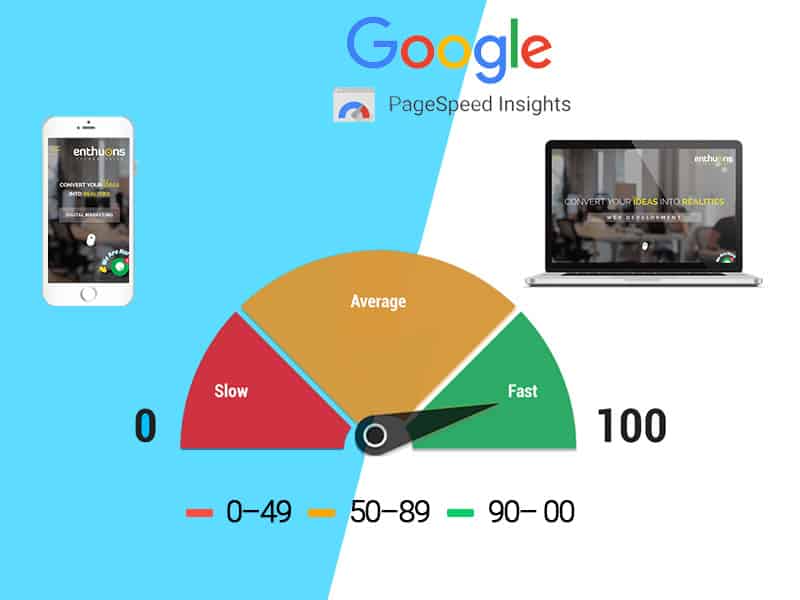
What Is Google Page Speed & Website load time

Microsoft MSHTML Remote Code Execution Vulnerability - vulnerability database

Spam and phishing in Q1 2021 - vulnerability database
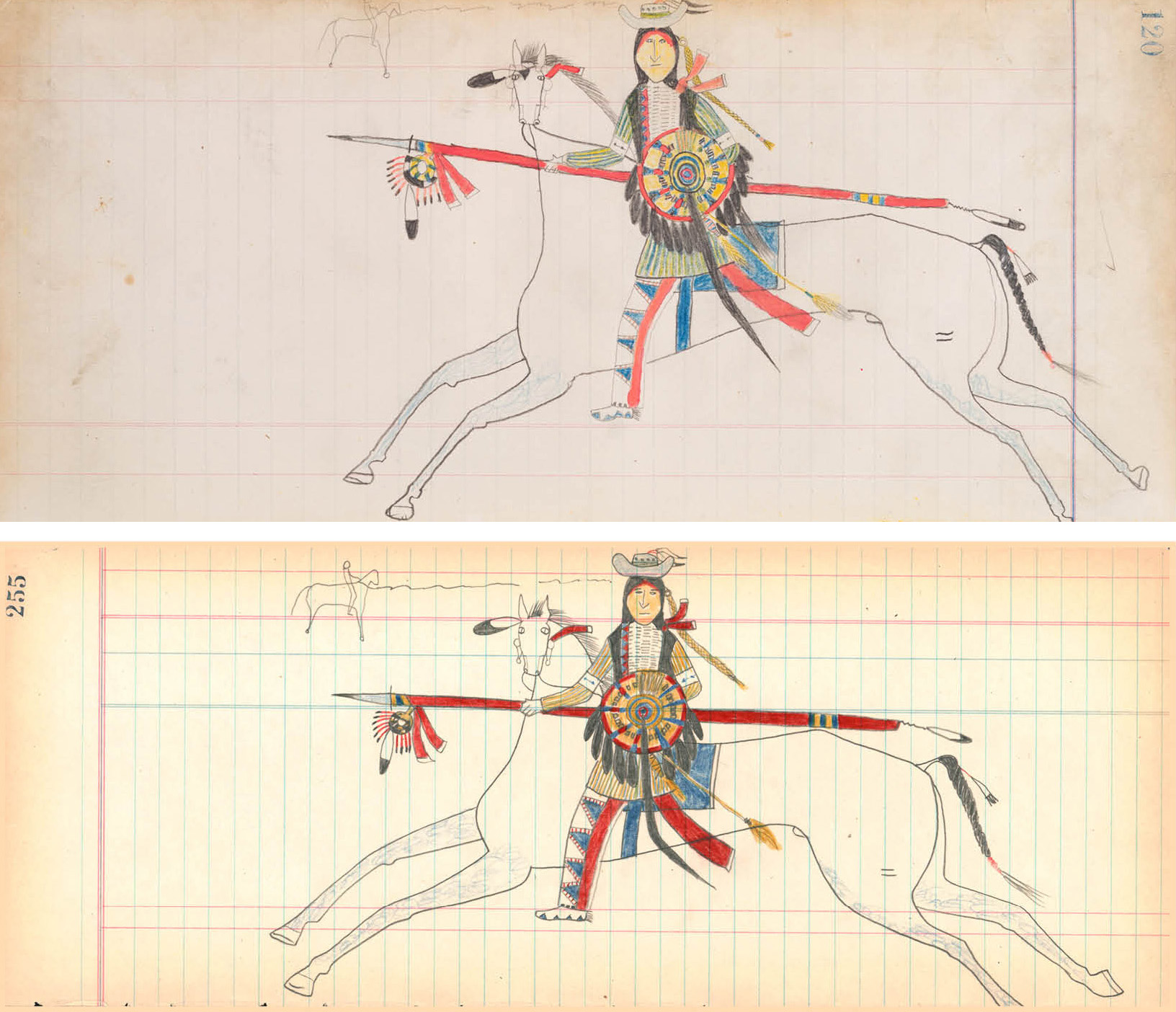
How Possibly Fraudulent and Forged Indigenous Art Ends up in Museums

Grossman LLP, Art Law Blog
TVO Original “There Are No Fakes” reveals a dark tale of

Ransomware-as-a-service: Understanding the cybercrime gig ec - vulnerability database
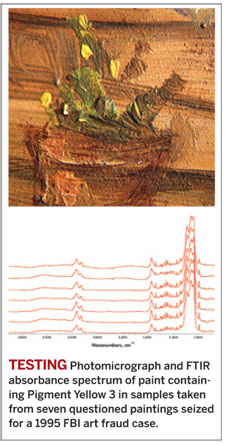
Fakes-Forgeries
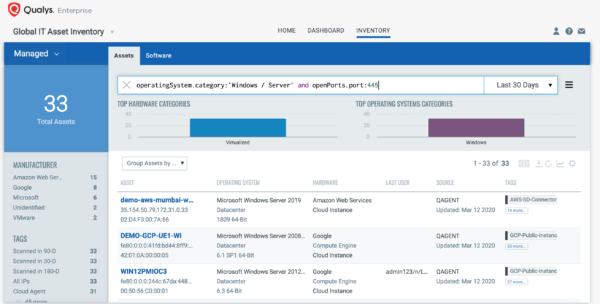
Automatically Discover, Prioritize and Remediate Microsoft S - vulnerability database
