
Midgård For a brighter tomorrow

A Complete Guide How to tell a real vs fake MCM BELT

How To Spot A Fake Gucci Belt In 2023 - Legit Check By Ch
scikit-learn-interactive-tutorial/test_with_solutions.csv at master · amueller/scikit-learn-interactive-tutorial · GitHub

How Just Opening A Malicious PowerPoint File Could Compromis - vulnerability database
I recently bought a Gucci belt (not from the Gucci website) and when I got it, it only had 19 serial digits on it. Is it authentic? - Quora

How to Spot a Fake Gucci Belt in 5 Ways (With Images)
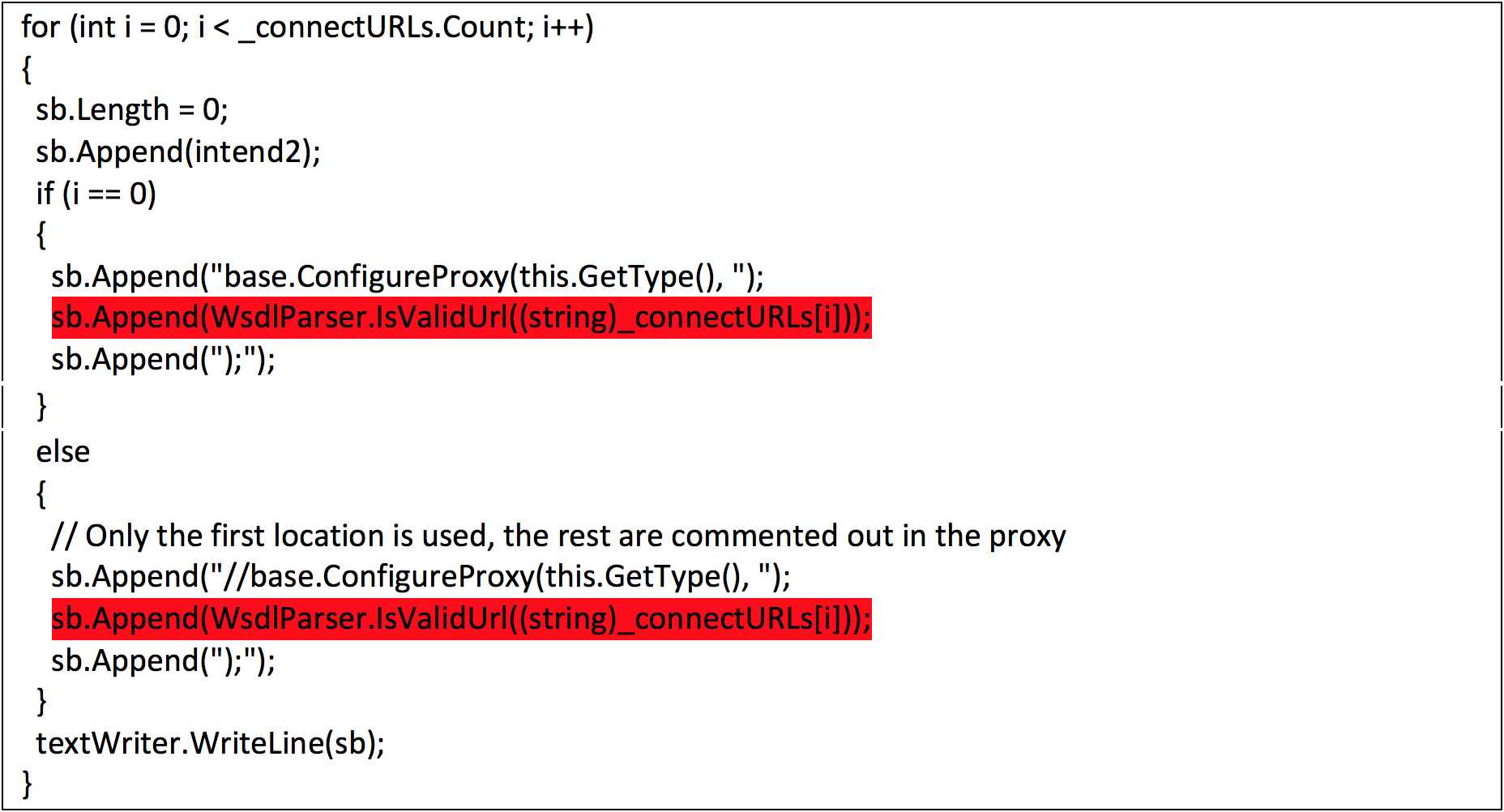
FireEye Uncovers CVE-2017-8759: Zero-Day Used in the Wild to Distr - exploit database

Real vs Replica Gucci HOW TO SPOT A FAKE GUCCI BELT

POWELIKS — A Persistent Windows Malware Without Any Installe - vulnerability database

REAL VS FAKE GUCCI BELT COMPARISON HOW TO SPOT A GUCCI BELT 2020(EASY)(POSHMARK SCAM)
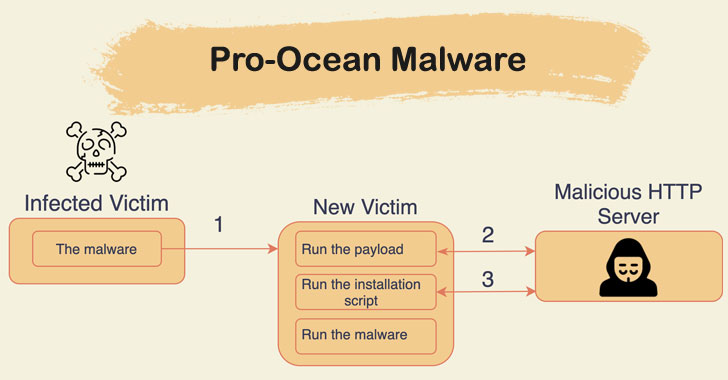
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se - vulnerability database
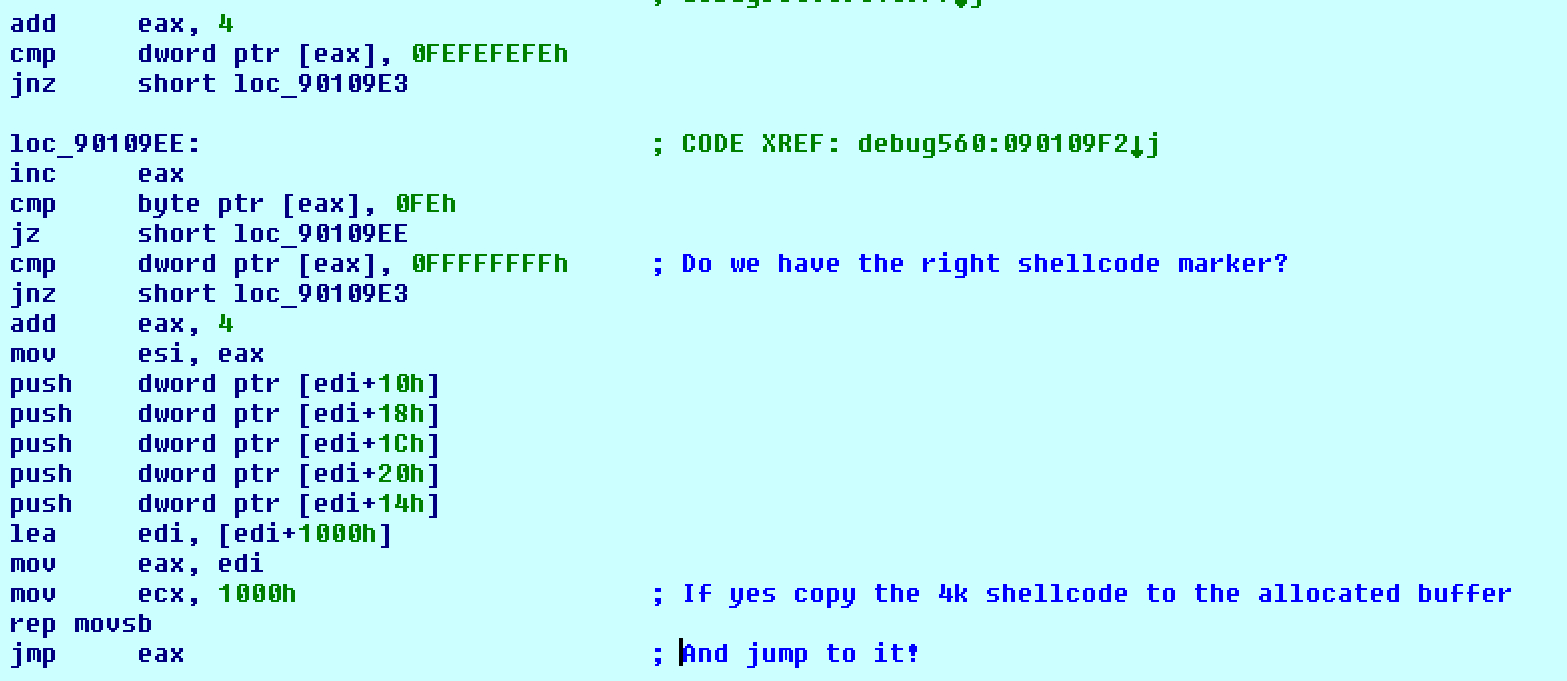
When combining exploits for added effect goes wrong - vulnerability database
